Talk:Cybersecurity
Creation of new article for cybersecurity[edit]
I suggest to create a separate article for cybersecurity to distinguish from information security and computer security, the explanation for this change in included in the following content:
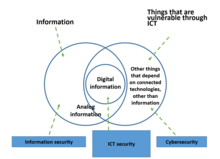
Cybersecurity should be differentiated from other types of computer security and information security, covering not only the protection of information but the infrastructure, services and supply chains dependent on information technology and communication systems. CISA defines it as the "art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information." [1]
Cybersecurity is defined by NIST as "Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation."[2]
The increasing use of information technologies in an increasing number of applications, not only for data or information management, but to support, automate and efficient work and activities of all kinds, applied to all productive, entertainment and personal use sectors has led to an exponential growth in the number of connected devices. In this way we find connected devices for the control and automation of home functions - called home automation - such as on and off lights, climate control and air conditioning, opening and closing doors, among others. In the same way in the business environment we find devices that control alarms, elevators, fire monitoring and control, room automation, access control of staff and visitors, and many other applications. Connected cars, medical devices – including some inserted into the patient body, such as pacemakers and insulin pumps – are increasingly coming to market, industrial controls, power, gas and other basic supplies.
It is related to information security and computer security, but also considers the protection of related infrastructure, products and services. Then cybersecurity is the protection of information and telecommunication technologies (ICT), the data processed and the infrastructure, products and services depending on them. [3]
The Information Systems Audit and Control Association (ISACA) defines cybersecurity as "the protection of information assets by addressing threats to information processed, stored, and transported by internet worked information systems"[4]
International[edit]

The International Telecommunication Union publishes the Global Cybersecurity Index[5] and measures five pillars for cybersecurity measured for the surveyed countries: five pillars:
• legal measures;
• technical measures;
• organizational measures;
• capacity development measures;
• cooperation measures.
Introduction to Cybersecurity
Cybersecurity is a vital and rapidly evolving subject that specializes in shielding pc structures, networks, and records from numerous cyber threats and assaults. As our international turns into increasingly digitized and interconnected, the importance of cybersecurity has in no way been greater.
In this advent to cybersecurity, we are able to explore the fundamental standards of cybersecurity, the importance of safeguarding virtual assets, and the risks posed through cyber threats. We'll delve into the distinctive forms of cyber assaults and the techniques employed through cyber criminals to take advantage of vulnerabilities.
Moreover, we're going to talk the important thing additives of a robust cybersecurity method, which incorporates the use of superior technology, steady coding practices, and employee consciousness and education. Understanding the significance of cybersecurity in each private and expert settings is vital for making sure the protection of touchy data and maintaining virtual privacy.
By the cease of this creation, you may have a foundational know-how of the cybersecurity panorama and the want for proactive measures to shield towards cyber threats. Whether you're an man or woman trying to safeguard your private data or a business owner searching for to defend essential belongings, the understanding won from this introduction will empower you to take proactive steps in fortifying your digital defenses against the ever-evolving threats inside the cyber realm.
What is Cyber Securityhttps://cybersecuritycode.blogspot.com/2023/07/what-is-cyber-security-your-guide-to.html?
Cybersecurity, often written as "cyber safety," is the practice of shielding computer systems, networks, gadgets, and information from virtual attacks and unauthorized access. It encompasses a range of technology, strategies, and practices designed to guard facts era (IT) systems and make sure their confidentiality, integrity, and availability.
The primary intention of cybersecurity is to prevent cyber threats, such as hacking, facts breaches, malware, ransomware, phishing, and Distributed Denial of Service (DDoS) attacks. These threats can have intense outcomes, including monetary losses, recognition damage, and compromise of touchy data.
Key elements of cybersecurity consist of:
Information Security: Protecting sensitive records and facts from unauthorized get entry to, amendment, or disclosure.
Network Security: Implementing measures to secure computer networks and save you unauthorized get entry to and records breaches.
Endpoint Security: Protecting person gadgets, including computers, laptops, smartphones, and capsules, from malware and other threats.
Application Security: Ensuring that software program and applications are unfastened from vulnerabilities that attackers ought to make the most.
Cloud Security: Implementing security measures to defend facts and applications saved in cloud computing environments.
Identity and Access Management (IAM): Controlling access to sources and records, ensuring that only legal users have suitable permissions.
Encryption: Using cryptographic techniques to encode information to protect it from unauthorized get entry to during transmission and storage.
Incident Response: Developing a plan to reply successfully to cybersecurity incidents and mitigate their impact.
Security Awareness and Training: Educating customers approximately cybersecurity fine practices and capability threats to sell a security-conscious lifestyle.
Vulnerability Assessment and Penetration Testing: Identifying and addressing security weaknesses via ordinary trying out and evaluation.
As the virtual panorama evolves, cyber threats hold to boost, making cybersecurity an ongoing and important challenge for people, agencies, governments, and businesses of all sizes. Adopting strong cybersecurity measures is important to guard touchy facts, keep business continuity, and protect against the ever-evolving cyber dangers in today's interconnected global. Personal Security- Safeguarding Your Digital Life — Preceding unsigned comment added by Azizulsohel (talk • contribs) 17:55, 31 July 2023 (UTC)
References[edit]
- ^ "CISA Cybersecurity". CISA security tips. CISA.
- ^ "NIST Cybersecurity". NIST Glossary. NIST.
- ^ Corona Fraga, Pablo (July 2019). Practical Guide for risk management in the age of cybersecurity. Mexico. p. 39. ISBN 978-607-474-479-8.
{{cite book}}: CS1 maint: location missing publisher (link) - ^ "ISACA Glossary" (PDF). ISACA Glossary. Retrieved 29 January 2022.
- ^ "Global Cybersecurity Index". ITU-T Global Cybersecurity Index. ITU-T.
Pcoronaf (talk) 17:15, 25 May 2022 (UTC)
Important of Cyber Security! Your Guide to Cybersecurity- Everything You Need to Knowhttps://cybersecuritycode.blogspot.com/2023/07/what-is-cyber-security-your-guide-to.html — Preceding unsigned comment added by Azizulsohel (talk • contribs) 18:05, 31 July 2023 (UTC)
Move discussion in progress[edit]
There is a move discussion in progress on Talk:Computer security which affects this page. Please participate on that page and not in this talk page section. Thank you. —RMCD bot 11:15, 4 July 2023 (UTC)
